Intigriti's March 2021 XSS Challenge
March 28, 2021
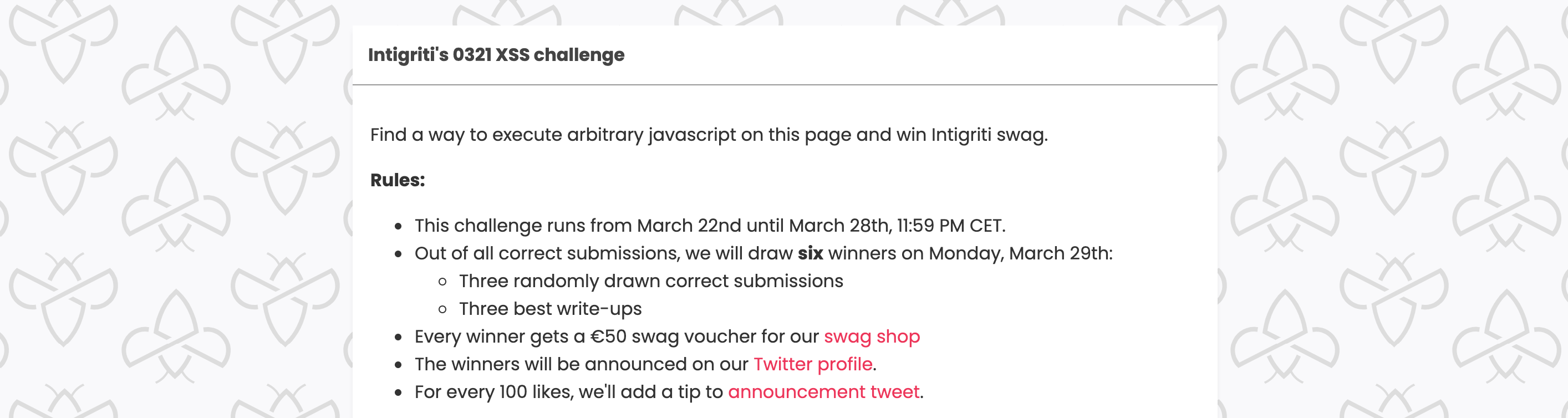
At the end of March 2021 the Belgian ethical hacking platform Intigriti hosted a new XSS (cross site scripting) challenge.
- I was not able to create a writeup in HTML but I uploaded a PDF containing my writeup that can be read below or downloaded: PDF
- I also created a small POC video that shows the XSS attack being delivered to the victim when visiting our webserver containing the exploit: POC Video
The POC video shows first the Intigriti page with the default note. Then the victim visits a regular website (google.com) like he is browsing the internet. After that the victim visits the attackers website and automatically the victim is redirected to the Intigriti page that now contains our XSS payload due to the CSRF token being bypassed. The attackers website redirect in the video takes 20 seconds but this is set like that for debugging purposes and can be done faster.
Embedded writeup PDF:
Latest Posts
- February CTF Challenge 2026 - Intigriti November CTF Challenge 2025 - Intigriti October CTF Challenge 2025 - Intigriti October CTF Challenge 2025 - Intigriti May XSS Challenge 2025 - Intigriti January XSS Challenge 2025 - Intigriti January XSS Challenge 2025 - Intigriti August CTF Challenge 2024 - Intigriti June XSS Challenge 2023 - Intigriti April CTF Challenge 2023 - Intigriti February XSS Challenge 2023 - Intigriti December XSS Challenge 2022 - Intigriti July XSS Challenge 2022 - Intigriti March XSS Challenge 2022 - Intigriti February XSS Challenge 2022 - Intigriti January XSS Challenge 2022 - Intigriti December XSS Challenge 2021 - Intigriti October XSS Challenge 2021 - Intigriti September XSS Challenge 2021 - Intigriti May XSS Challenge 2021 - Intigriti March XSS Challenge 2021 - Intigriti November XSS Challenge 2020 - Intigriti May XSS Challenge 2020 - Intigriti KIBA - Try Hack Me